Protecting yourself online

Online security
Online security has never been more important. As consumers we’re doing more and more online than ever before. Most people shop and bank online these days, meaning the security of your accounts is of vital importance. In a lot of cases, the password you enter at sign-in is the only level of security protecting your online account.
Security is not a single line of defence; it must consist of a layer of good habits and technical measures – such as keeping strong, unique passwords and running regular anti-virus scans.
Below are a few tips to keeping your online accounts secure:*
Password Security
Do not reuse passwords between websites
• It’s very tempting to use the same password you use for one online account with another website, but it is absolutely critical these days that you don't fall into this habit.
• Hackers know that a great deal of people use the same (or similar) passwords for most of the accounts they use online, so when they get hold of a password for one account, they will often use an automated process to try and log in to as many online services as they can with that password.
• In that scenario, if your email account is compromised and you use the same password for an online shopping website, as well as your social network profile and your online bank – the hacker will be able to login to all of those services.
• The problem with ensuring that you do not reuse passwords across different websites is that you may find it difficult to remember all your passwords. We recommend using a secure reputable password manager to hold your passwords for you – see 'Use a password manager' below to learn more.
Use strong passwords
• Strong passwords use a combination of uppercase and lowercase letters, numbers and; if possible; special characters. This makes it very difficult for automated programs and hackers to guess your password. Check out the 'Understand how accounts become compromised' section to understand how account passwords are often guessed.
• Do not use real words in your password. Hackers will often use an automated system to attempt to use dictionary words as your password, so if your password consists of a dictionary word – there’s a good chance they’d be able to login and compromise your account.
• A good way of securing your password is to substitute some of the letters in your password for numbers. For example, instead of writing the letter 'S', you could use the number 5, which looks very similar. The same applies for other letter and number combinations.
Never share your passwords with anyone
• It may sound like a basic point, but it’s one of the most important. Never share your password with anyone. You may inherently trust that person, but you have no guarantee that they follow adequate security precautions and you can therefore not be certain of the security of the password that you have shared.
• For example, if you provide your password to someone who enters it into a computer that is infected with malware, or they write it into a book of passwords that they keep – your defences to online fraud are instantly weakened.
• This includes speaking to professionals like Technical Support Agents, or your computer engineer.
Change your passwords regularly
• It is good practice to regularly change the passwords you use online, even if you use strong, unique passwords and don’t have any reason to believe your account is compromised.
• Online accounts can be compromised (sometimes through no fault of your own) and hackers may just monitor your online accounts – such as your email address, waiting for something valuable to appear, such as a password reset email for your online bank.
• There may be no visible symptoms that your account has been compromised, so changing your password regularly is a good way of minimising the risk of this happening.
• It’s up to you how often you change your passwords, but it's generally a good idea to change them every few months.
Use a password manager
• Password managers are software applications that store your login information for all the websites you use and help you log into them automatically. They encrypt your password database with a master password – the master password is the only one you have to remember.
• This allows you to have strong, unique passwords for all your online accounts – meaning you don’t have to remember them.
• When using a password manager, it is vital that you use a completely unique and very complex master password, and use two-factor authentication where possible. If your password manager’s master password is obtained by a third party, they could then gain access to all of your online accounts from there.
• Be sure to use a reputable password manager by researching and reading user reviews before downloading/installing.
Review your password recovery questions
• Most online services have password recovery options that can be used to regain access to your account if you forget the password for it. These questions normally ask for things like your favourite football team or your mother’s maiden name.
• Ensure that you make these questions and answers as hard as possible to guess and if possible, select questions that only you will be able to answer.
Run Antivirus scans across all of your devices
• Ensure that you have anti-virus software installed on all the devices that you use. Computers, tablets and mobile phones can all be infected with malware.
• Mobile devices and computers running Apple Mac OS and Linux are less likely to be infected than a Windows computer, but there’s still malware available for them – so it’s important that you run regular virus scans across all devices just for peace of mind.
Keep all of your devices up-to-date
Here’s a big one that seems to slip under a lot of people’s radar. Software applications often have vulnerabilities in their code that can be exploited by a third party in order to perform malicious attacks as well as stealing personal information. Software developers will fix vulnerabilities in their applications once they’ve discovered them, but in order for your devices to benefit from the fix, you need to update the application to the latest version.
This also goes for operating system updates, be it on your computers or mobile devices. If there’s a software update available, it is very important that you update – running older versions could mean you are susceptible to attack.
Authentication and Encryption
Use two-factor authentication where possible
Some online services offer a second form of authentication where possible, normally by sending a text message to your mobile phone to confirm you’ve logged into your online account from a device you haven’t used that service on before.
Use two-factor authentication wherever possible. A number of online services offer this as an option but it’s not enabled by default. Using this form of authentication adds a second layer of protection in case your password is obtained by a malicious third party.
Encrypt your sensitive information
This may not be applicable to everyone, but encryption may come in handy if you have any personal data that you want to protect from falling into the wrong hands - if your computer is stolen or your computer is taken over by malware.
Encryption is the most effective way to properly secure your data. To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it.
There are a number of applications available that can be used to encrypt files. Some computer operating systems have options to encrypt your hard drive’s contents when the machine is not being used.
Also, a number of password managers include secure note functions, which allow for text to be held securely.
Keep physical security in mind
A lot of incidents where personal or financial information has been subject to theft involves a physical security failure, often by the victim.
• Ensure that you lock your computer or log out of it when you’re not using it, even if you’re just leaving it for a minute or so to grab a coffee
• Never set your web browser and other applications to remember your account passwords unless you are the only person that uses that computer (or profile if the computer has user profiles setup)
• When using a computer you share with others, always log out of any online services after you stop using them
• Don’t write your passwords down on paper. Burglars are becoming increasingly aware that people keep passwords written down, and they exploit this.
• Never provide information or data to someone you do not trust, if you have any suspicions that someone is not legitimate, ask for identification or contact the company they claim to represent
Understand how accounts become compromised
Online accounts can become compromised in several ways, below are a number of the most common techniques used by hackers:
• Malware – Often referred to as viruses, malware is malicious software designed to steal personal/financial data or use your computer in order to commit abuse such as participating in network attacks. Malware is often installed without a user’s knowledge, and is often bundled with illegal downloads of media or on less than reputable websites
• Phishing – Malicious third parties may send emails or other types of messages that are designed to look like they have been sent by a reputable company or individual in order to obtain information from you or to infect your machine with malware. An example is an email that appears to come from your bank, asking you to update your online password
• Social Engineering – This is where a malicious third party uses social techniques to trick information out of someone or to trick someone into doing something for them. A good example is someone calling you advising they’ve noticed your computer is infected with malware, and they require access to your computer in order to resolve it. Once given access, they will be able to access your machine and can install malware, extract personal information and even hold your data to ransom
• Password attacks – A password attack is when various techniques are used to gain access to a system or service that requires a password
– Dictionary/Rainbow attacks - Common techniques include an automated process attempting commonly used password or dictionary words, trying them one after another until access is gained.
– Brute force attacks - Some automated process are also used to try every possible combination of letters, numbers and special characters in order to eventually guess the correct password for that account.
– Password re-use attacks – Hackers know that a great deal of people use the same (or similar) passwords for most of the accounts they use online, so when they get hold of a password for one account, they will often use an automated process to try and login to as many online services they can think of with that password.
• Vulnerability exploitation - Software applications often have vulnerabilities in their code that can be exploited by a third party in order to perform malicious attacks as well as stealing personal information
• Data leaks - Malicious hackers rarely keep stolen data to themselves, they will publish usernames, passwords and any other data they’ve obtained online for the world to see. This will then trigger other malicious third parties to perform identify theft or access your online accounts using the credentials that have been leaked online.
• These fixes are provided as a courtesy. We are not responsible for any problems encountered while following this advice and unfortunately we are not able to provide any technical support for these issues.
How to protect your computer
Protecting your computer is the first step to online safety. To find out how best to do this, follow our handy tips below.
Get anti-virus software
• You really need this to keep your computer and documents from being damaged by viruses. Once installed, make sure the anti-virus software is set to update and check your computer automatically.
• Everyone should be able to enjoy being online without worrying about viruses, malware, phishing and other nasties. That’s why we offer all our customers award-winning Virgin Media Internet Security on unlimited devices. You’ll pay nothing for 3 months then just €4 a month thereafter. So you can relax knowing you're safe and secure online. For more details check out Introducing Virgin Media Internet Security.
Use spam controls
• Spam is unwanted and unsolicited email. Virgin Media email has automatic spam controls which block email that has been identified as spam.
Use a firewall
• If you have a broadband connection, your computer is always connected and at risk from intrusion. A firewall prevents others from accessing your computer (and therefore your personal info). It puts a block in place and keeps your data safe.
Keep my computer physically safe
• Make sure you back up all your data regularly. Virgin Media offer online Backup & Storage to help you keep all your data and documents safe and secure. Always ensure your home or office is secure from potential break-ins.
• Also, take care that your computer is in a safe place where it won't get wet, knocked over, or too hot. Try to keep dust from building up on the vents and unless you’re using a laptop, never try to move your computer while it is on.
Protecting your identity
How can I help keep my details safe?
Be careful if someone you don’t expect gets in touch and asks you to log into your online accounts, make a payment or give them any personal information.
This might happen over the phone, face-to-face, or online. If you’re not sure, politely decline and contact the company they’re from using an email or phone number that you know belongs to that company.
Don’t share too much personal information on your social media, and be sure to check your privacy settings.
Never tell anyone your password or PIN, and make sure it’s not easy to guess. For example, don’t use your year of birth, or your date of birth.
Finally, make sure any documents that contain your personal details are shredded before you throw them away.
Social media scams
Criminals often use bogus celebrity endorsements in order to scam their social media followers into cyber scams, such as “get rich quick” schemes and investment schemes that appear to have been endorsed by famous people.
Linkedin members are also being targeted by fraudsters who have been hacking into legitimate users accounts and sending victims what appear to be genuine emails and messages from the victim's known trusted contacts or celebrities. The messages/emails ask them to view a document via OneDrive, which displays details of a hacked US celebrity’s website. Once the link is opened, it redirects the victim to a website and the victim’s username and password is obtained by the fraudster.
Other LinkedIn members are being approached by individuals claiming to be an employee of a particular company.
How to protect yourself
• Be aware that celebrities such as Richard Branson will generally not direct message you on social media platforms.
• If it sounds too good to be true, it probably is.
• Don’t click on the link offered on the pop-up ad.
• Check if the company has an official website and social media accounts.
• Check on Google and the Internet search tools to see if any scams have been reported.
• Limit the contact information on your LinkedIn profile.
• Make sure you turn on LinkedIn’s secure browsing mode.
• Be cautious when applying for jobs via social media websites.
• Never accept connection requests from people you don’t know.
• Ensure your operating and security software are up to date.
• Ensure your passwords are strong and change them regularly.
Concerned you have been scammed?
• If you have been a victim of fraud, report it to An Garda Siochana on https://www.garda.ie/en/crime/fraud. However, if debit cards, online banking or cheques are involved in the scam, your first step should to contact your bank or credit card company.
Vulnerable victims of fraud
People who can be especially vulnerable to scams include older people and people with mental health problems, learning difficulties or dementia.
Elderly people have savings, time and trust - three reasons why scam artists will relentlessly prey on them. They are vulnerable and often alone in the house without a voice of reason or second opinion.
Types of scams targeting vulnerable people:
• Pension Scams
• Investment scams
• Lottery Scams
• Romancing scams
• Doorstep scams including diversion fraud
• Identity Theft
• Credit card fraud
• Will Writing services
• Phishing calls
• Cold Callers
Useful link
Age Action IE https://www.ageaction.ie/sites/default/files/29253-age_action_a5_scams_and_frauds_leaflet_web.pdf
If you have been a victim of fraud, report it to An Garda Siochana on https://www.garda.ie/en/crime/fraud. However, if debit cards, online banking or cheques are involved in the scam your first step should to contact your bank or credit card company.
Younger internet users can also be vulnerable online. At Virgin Media we are committed to safely online, which is why we offer Parental Controls as a service to all our broadband customers to help protect younger members of their household from unsuitable content. The additional links we’ve included below will also advise on how to keep children safe on the internet. Software can be downloaded from the relevant app store and many smartphones have local controls also.
Android
https://www.safesearchkids.com/
Apple
Working from home - how to protect yourself and your employees
• Never respond to or act upon emails requesting to verify or update personal or financial information. These emails are crafted to look like correspondence from a trustworthy source (Revenue, Banks, Government bodies.) Take a screen shot of the email, delete it and make you IT department aware of the receipt of a phishing email.
• Never click into any embedded web link in an email that comes from a source you don’t know. This could install malware, ransomware or a virus on your computer.
• Make sure any request to transfer payments from/to Financial Controller/CEO/Third party are legitimate emails, by verifying with the person separate to the email, before making the payment.
• If you receive an email requesting your bank details, check if it's from a legitimate source, Pay attention to the font, spelling, punctuation, email address. Don’t share unless you have verified its authenticity.
• Be wary of suspicious phone calls asking you to validate your account number for a specific service.
• Never give any usernames or passwords out over the phone or by email
• Don't allow anyone to remotely log onto your PC if you don't know who they are.
• Use a secure internet browser.
• Ensure your passwords are strong and changed regularly.
• Do not access confidential information on open WiFi like cafés, hotels etc.
• Always use up to date anti-virus protection software on your laptop, tablet or mobile phone.
• Be aware of how much information about you is available on social media, like your birth date, hometown and school details. This information is useful to Cyber criminals.
• Use a web filter that blocks malicious websites, and deploy inbound spam filtering.
• Training is key. Regularly make sure everyone in the organisation is aware of what phishing scams look like, and the types of attacks they may face. Make sure they understand the risks and how to address them.
• Read all URLs from right to left. The last address is the true domain. Secure URLs that don't use https are fraudulent, as are sites that begin with IP addresses. If the domain of the link to which you are being directed doesn't match the purported company domain, then the link is a fake.
Fraudulent pop-up ads
• A fraudulent pop-up ad is a scam that can be sent to your device over a web page through your internet browser. The fraudsters will tell victims that there is a problem with their device or a security threat.
• This scam can take many forms, where fraudsters use different scenarios such as calling a number to pay for technical support or clicking on a link to resolve the issue.
• These pop-ups can be dangerous to the victim. The fraudsters can gain access to your credit card information, and can often gain access to your phone itself. They can do this by advising the victim that their device is infected with multiple viruses and that it can be resolved by buying their antivirus software.
• You should always be vigilant when looking for antivirus software, and go with known and trustworthy software. Fraudsters often pay to have their ads, website and phone numbers on the top of a search engine.
What do these ads look like?
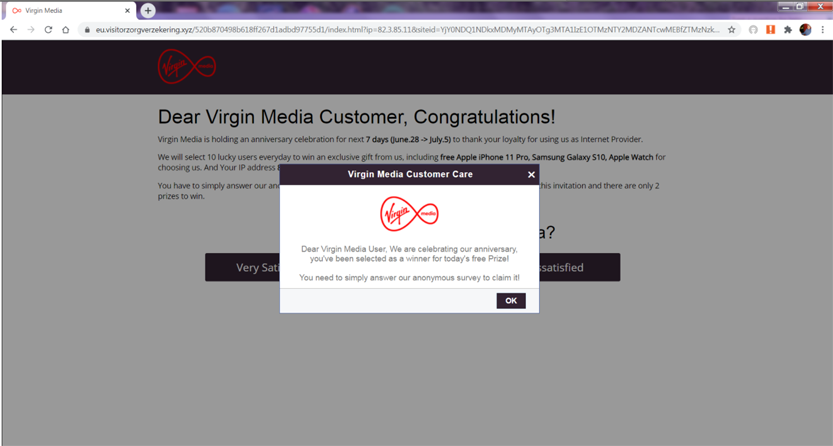
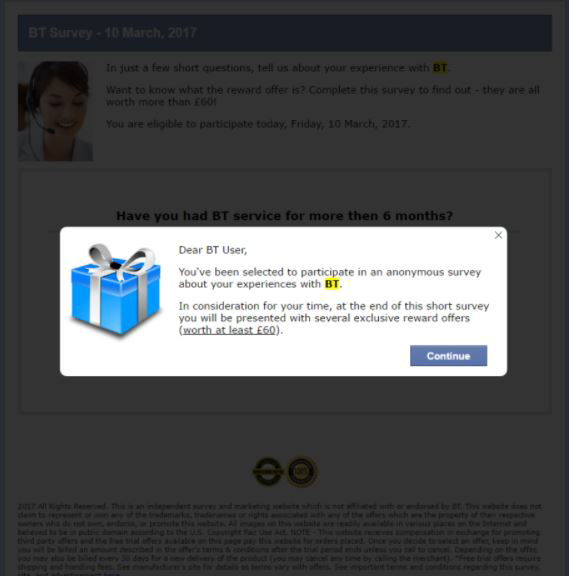
How can I prevent this from happening to me?
It is important to be alert to this kind of fraud and know the warning signs for fraudulent pop-ups.
• Warning messages with vague promises or reassurances may be an indicator, like 'safeguard your data' or 'we can protect your privacy'
• If a deal or prize is too good to be true, then it probably is. Fraudsters will hold competitions such as “Win an iPhone for €1”, where they get you to enter in your card details to pay the €1, the fraudster then has your credit card details.
• If you receive a pop-up stating that it has detected your device has a virus, don’t click into it. Instead use the clean-up system on your device itself. If there are any viruses, your device should pick it up.
• If you suspect the pop-up ad is suspicious, check the company out on a search engine. Real companies will have a good variety of information on their site and others.
• Keep an eye out for spelling and grammar mistakes on the pop-up ads. Check the messages carefully and ignore those that have an obvious spelling or grammar mistake.
What you should do if you see a fake pop-up ad?
If you spot a fake pop-up ad, you should do the following:
• DO NOT click on it or open it.
• Close your browser immediately. Do not call any phone number provided.
• You may need to force your browser to quit.
• Sometimes the 'Close' or the 'X' on the ad can open the virus, be vigilant.
• When restarting your browser, do not reopen your previous tabs and make they have all been removed. Clear your browser cache.
• Don't click the link you visited immediately before you got that virus warning.
• You should run a systems scan, to detect any virus on the device. Be sure to do a complete scan.
• You can turn on your pop-up blockers on your device. Most fake virus warnings come in pop-up form. This can be stopped by turning on the pop-up blockers in your internet browsers.
• Be careful when surfing the web, ensure the sites are safe; they will usually have an image of a lock on the top left hand corner or the URL will begin with https:// to show they are secure.
• Even if the pop-up looks authentic, you should never reach for your credit card details. No real security software will charge you to deal with an individual virus threat.
How do I turn off pop-up blockers?
Computers/Tablets/Laptops:
• On your computer, tablet or laptop, open Chrome.
• At the top right click More> Settings
• Under the 'Privacy and security' tab, click on 'Site Settings'
• Click 'Pop-ups and redirects'
• At the top, turn the setting to 'Blocked'.
• This can also be reversed to allow them, by turning the setting to 'Allowed'.
iPhones:
• Go to the Settings in Safari and then turn on 'Block Pop-ups'.
• Then go to the Safari settings and turn on the Fraudulent Website Warning.
• You should also keep your phone updated, this can be easily be checked by going to Settings>General> Software Update
Androids:
• On your phone open the Chrome app.
• On the right of the address bar click on >More > Settings
• Click on Site Settings > Pop- ups and redirects
• Turn Pop-ups and redirects off.
• This can also be reversed to allow them, by turning the setting to back on.


